Cybersecurity Services
CYBERSECURITY
Protect Your Business With Our Advanced Cybersecurity Solutions
In an era where cyber threats are constantly evolving, safeguarding your digital assets is more critical than ever. Our comprehensive cybersecurity services offer robust protection and peace of mind, ensuring your business stays secure.
CYBERSECURITY
24/7 Monitoring and Alerting
Our round-the-clock monitoring and alerting services offer real-time protection against cyber threats. Key features include:
- Continuous Surveillance: Monitor your network 24/7 to detect and respond to threats immediately.
- Instant Alerts: Receive real-time alerts for suspicious activities and potential breaches.
- Rapid Response: Our expert team is ready to take swift action to mitigate risks and minimize damage.
- Advanced Threat Detection: Utilize cutting-edge technology to identify and neutralize sophisticated threats.


Security Awareness Training
Phishing attacks are a major threat to businesses. Our phishing exercises help your team recognize and avoid these scams. Key benefits include:
Simulated Attacks
Conduct realistic phishing simulations to test your employees’ vigilance.
Performance Tracking
Measure and improve your organization’s resilience to phishing attacks.
Awareness Building
Educate your team on identifying and avoiding phishing attempts.
Customized Scenarios
Measure and improve your organization’s resilience to phishing attacks.


CYBERSECURITY
Cyber Training
Empower your employees with the knowledge and skills to defend against cyber threats. Our comprehensive cyber training programs offer:
- Interactive Learning: Engage your team with interactive, hands-on training modules.
- Expert Instruction: Learn from cybersecurity experts with extensive industry experience.
- Regular Updates: Stay ahead of evolving threats with up-to-date training content.
- Certification Programs: Validate your team’s cybersecurity skills with recognized certifications.
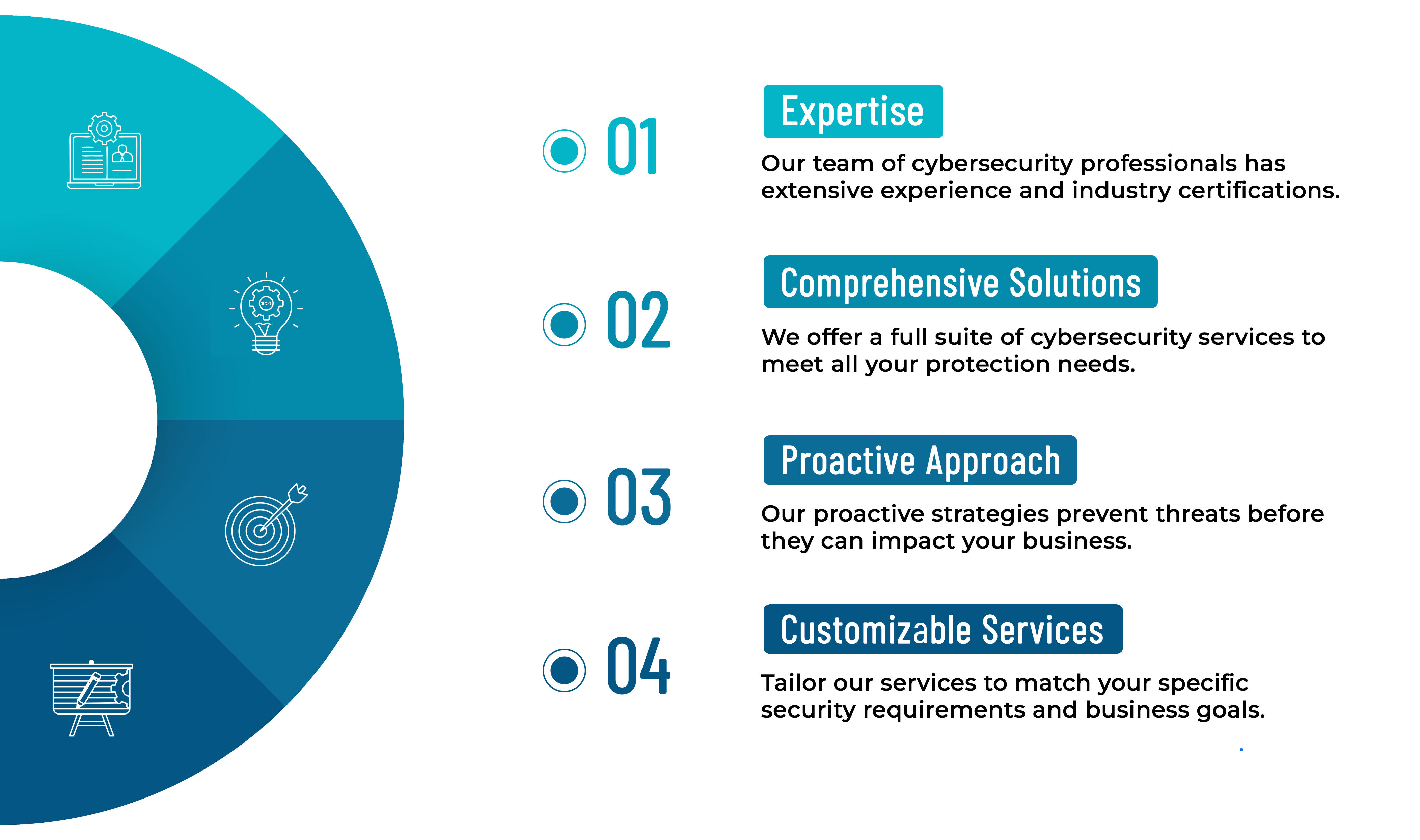
BENEFITS
Why Choose Our Cybersecurity Services?
Choose MX2’s Cybersecurity Services for expert, proactive, and customizable protection that covers all your security needs.
SECURE YOUR BUSINESS TODAY
Don’t leave your business vulnerable to cyber threats. Partner with us for top-tier cybersecurity services, including 24/7 monitoring and alerting, phishing exercises, and comprehensive cyber training. Contact us today to learn how we can help you safeguard your business and ensure peace of mind in the digital landscape.
Take the first step towards a secure future. Reach out to our cybersecurity experts and fortify your defenses now.
We're Here to Help
(408) 940-0040
Email Support
Our friendly support staff are ready to help resolve your IT problems! Fill out the form on this page and provide as much detail as possible, and one of our helpful team members will be in touch.
Operating Hours
Mon – Fri 8:00 – 5:00 PDT

